
The Treasury Department has warned U.S. publishers that their editors are not allowed to alter the text of any books they’re reprinting from “disfavored nations” — such as Iran, Libya, or Cuba. That means that yes, they’re allowed to print books that came from those countries, but they cannot fix typos, edit text, or even add pictures and captions. The punishment for breaking the law? A half-million-dollar fine and up to 10 years in jail. As the New York Times reports today:
Nahid Mozaffari, a scholar and editor specializing in literature from Iran, called the implications staggering. “A story, a poem, an article on history, archaeology, linguistics, engineering, physics, mathematics, or any other area of knowledge cannot be translated, and even if submitted in English, cannot be edited in the U.S.,” she said.
“This means that the publication of the PEN Anthology of Contemporary Persian Literature that I have been editing for the last three years,” she said, “would constitute aiding and abetting the enemy.”
Apparently these laws have genuinely begun to affect scientific discourse:
These days, journals published by the engineering institute reject manuscripts from Iran that need extensive editing and run a disclaimer with those they accept, said Michael R. Lightner, the institute vice president responsible for publications. “It tells readers,” he said, “that the article did not get the final polish we would like.”

Man, the guys at Benrik have created some sheerly hilarious stuff. I posted below about their World Mood Chart, but then I started looking around the rest of their site — and I found The World’s Longest Poem.
Go there, enter your own line of up to 60 characters, and it will automatically be added to the poem. It’s already 8,662 lines long (I dumped the text into an Excel spreadsheet to find out), though that includes a place in the middle with the line “yeti, dodo, chocolate muffins all dead but where’s the care” repeated 172 times in a row, which is either a bug in the program or a contributor making some truly opaque literary statement.
Here’s the text leading up to my contribution; the last line is mine:
You’ve got to stay at the YMCA!
unbornchikkenvoicesin my head?
And then I ran. Faster than any had thought possible.
and it all smelt like chicken
then father wispers, “Go to hell.”
but Reader, I was already gone.
Years ago, I got the idea for an Internet Mood Ring. I thought it’d be fun to write a little application that would sit in the corner of your screen, showing you two small buttons. They would mimic the color range of a mood ring — they’d glow black for a “bad” mood, then gradually lighten through reds and oranges and greens until they glowed blue for a “good” mood. The first button represented your mood; you’d click on it to bring up a slider, and slide it to represent the right color. The other button would represent the average of all the other moods of all the other users of the application. That way you could watch as the world’s mood shifted and changed during the day — and you could also, in a quick glance, compare your mood to that of the world at large.
I actually wondered if this wouldn’t produce some really weird Heisenbergian feedback effects; if you looked at the buttons and realized you were feeling better than the rest of the world, would that make you feel better still, causing you to dial your personal mood higher, thus causing the overall mood of the world to improve? And if everyone in a better-than-average mood did the same thing, wouldn’t that have a distortion effect on the world’s mood — bringing it higher? Or would the same thing happen in reverse: Maybe the people who realized they were lower than average would get even more depressed, dial themselves lower, and thus drag the average back down.
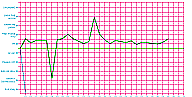
Anyway, I was too lazy to do anything about this. But I was pleased to find out the fine folks at Benrik had roughly the same idea — and they actually pulled it off! Go to the World Mood Chart, input your mood, and it’ll generate chart showing you how the mood of the world has gone up and down that month.
The chart above is for February. Clearly, something happened on Feb. 7 that just totally harshed the world’s mellow, because the mood dropped to somewhere between “Mad As Hell” and “Deeply Depressed”. Any idea as to what went on that day that could have shifted the mood of the entire planet?
(Thanks to Plastic Bag for this one!)
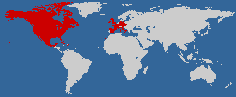
Go to World66 and click on a list of all the countries you’ve visited. Then it’ll generate map of the world showing where you’ve been in red. It’s an interesting experiment in geopolitics, because if forces you to realize how big the world is and how little of it you’ve seen — if you’re like me, that is. My map mostly-white map is above.

There’s an extremely cool test over at the BBC’s web site, where they play you video clips of 20 people smiling and you try to guess which ones are fake. Apparently, most people are bad at this, possibly because society would pretty much implode if we were knew just how miserable most of us are most of the time. I got only 13 out of 20 right.
In case you’re wondering how to spot a fake smile, the BBC has some suggestions — based on analyzing the physiology of smiles:
Fake smiles can be performed at will, because the brain signals that create them come from the conscious part of the brain and prompt the zygomaticus major muscles in the cheeks to contract. These are the muscles that pull the corners of the mouth outwards.
Genuine smiles, on the other hand, are generated by the unconscious brain, so are automatic. When people feel pleasure, signals pass through the part of the brain that processes emotion. As well as making the mouth muscles move, the muscles that raise the cheeks – the orbicularis oculi and the pars orbitalis – also contract, making the eyes crease up, and the eyebrows dip slightly.
Lines around the eyes do sometimes appear in intense fake smiles, and the cheeks may bunch up, making it look as if the eyes are contracting and the smile is genuine. But there are a few key signs that distinguish these smiles from real ones. For example, when a smile is genuine, the eye cover fold - the fleshy part of the eye between the eyebrow and the eyelid - moves downwards and the end of the eyebrows dip slightly.
This reminds me of my nearby McDonald’s, which I frequent way too often for my own good. About two months ago some manager put up a sign saying “If we don’t smile while we serve you, tell us and you’ll get a free hash browns or small fries with your next meal!” Beneath that it reads something even more sick, like “Go ahead — we love it when you catch us!” The first time I saw it I thought, christ, that can’t be real; that has to be some particularly subtle form of culture jamming. But it’s real, and were I to actually take the managers up on their offer, I could basically feed myself entirely for free off the sadness of McDonald’s employees, because in the last month I swear to god I haven’t seen a single cashier flash a smile once. Not even, dare I say, a fake one.
Slate just published my latest video-game colum: “Lost in Translation: Why Japanese gamers love avenging Pearl Harbor.” It’s about Medal of Honor: Rising Sun, one of the first war games to put you in the shoes American marines as they attack Japan in revenge for Pearl Harbor. The thing is, when Electronic Arts released the game in Japan, game reviewers loved it — even though the game requires that they repeatedly kill their virtual fathers and grandfathers, in a war that is still a rather touchy subject.
I try to explain the game’s popularity in Tokyo. You can read the piece online, but here’s a taste of my argument:
This leads to a surprising facet of game psychology: Really hard-core gamers often look past the cultural “content” of a game. They’re mostly worried about a more prosaic concern, which is whether the game is fun. The geopolitics of a game melt away as players, like philosophers musing on their favorite platonic solid, ponder gameplay in the abstract.
We’re accustomed to thinking that a piece of entertainment is nothing but its cultural content. A movie or TV show is just what you see on the screen. But a game is also about play, and play is invisible. That’s why outsiders are often puzzled by the success of games that would appear to be nothing but screamingly offensive content. They can’t see the play. Sure, you’ve got raw guts flying around — but for the player, part of the joy is in messing with physics (even if that happens to be bullets and shoulder-launched grenades) or with strategy (even if that’s figuring out how to starve a village).
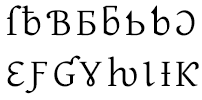
One of the interesting cultural problems of the Internet is that most fonts aren’t created to display more than one or two languages. If you visit foreign-language sites, you’ll notice that you’re always having to download “language packs” so that your browser can display the words correctly, with all the characters unique to the country’s language.
Victor Gaultney, a font designer, decided to tackle this problem by creating the Gentium typeface. His mission, as he describes it, is:
Gentium is a Unicode typeface that contains Roman, Greek and Cyrillic characters, including many characters seldom seen in even the most ambitious typefaces. Far from being a luxury, these characters are needed to write many of the over 6,000 languages thought to exist in the world.
He’s not quite there yet; Gentium only covers the Roman, Greek and Cyrillic scripts, which are historically pretty closely linked and thus typologically similar. It’ll be a while before he starts including the script for minor dialects spoken primarily in Ulan Bator. But nonetheless, the project is fascinating because it highlights an interesting point: That fonts are political, or at very least, have political implications. There’s a great interview with Gaultney on his site, in which he talks about how a font can affect global discourse:
Gentium has managed to break down some of the barriers between people. There used to be a wide gulf between the greater publishing, academic and multilingual communities. Publishers would hesitate to do work in unusual languages because the available fonts were so poor. Academics had to do their own thing because the industry did not support their needs. Multilingual publishing has often been a constant struggle with incompatible solutions of varying quality. Now everyone can use the same font — and get excellent quality, readable, attractive text.
What’s particularly cool is that he’s made Gentium free for download; you can get a copy of it here.
(Thanks to Snarkmarket for this one!)
Oh man. There are only two guys aboard the International Space Station, and on Monday they will be going on a space walk simultaneously. So the Station — a leaky Edsel in bad need of servicing — will be screaming through the howling aether on autopilot, while these poor saps bounce around outside and pray to god nothing breaks.
This sounds completely deranged to me, but apparently the Russians talked NASA into it. According to today’s New York Times:
At first, some NASA officials were uneasy about leaving the station unmanned for spacewalks, but Russia said the walk to be done this week was necessary to maintain some outside scientific experiments and to examine the exterior of the station. Russian officials also noted that they had made 50 spacewalks from their previous space station, Mir, with no one left inside.
I have to admit, I’m impressed. They did 50 spacewalks while Mir — which was basically an empty can of Lysol with retrorockets — flew unmanned? Say whatever you want about Russia, but their scientists have nerves of steel. How the hell did the U.S. win the cold war, anyway?
For decades, the military has been trying to figure out ways to keep soldiers awake and alert in the field — for days at a time. Back in the 60s, that meant some pretty hair-raising experiments with everything from bennies to LSD.
These days, the military is looking to the private sector to find out if anyone is developing a high-octane version of No-Doze. It’s no wonder they’re putting out feelers; after all, we civilians are buying an increasingly large number of performance-enhancing pills, herbs, and “smart drinks”. Many of these are total snake oil, as the New Yorker ably reported last week, but it hasn’t stopped the supplement industry from booming. Indeed, one could note the gorgeous symmetry of these trends: Outside of 22-year-old Ohio soldiers frantically dodging shrapnel-mines in Iraq, the main group of Americans who are trying to stay alert for 72 hours nonstop are crazed Gen-X yuppies gulping ginseng energy-tablets by the fistful. Be all you can be!
But je digresse. The whole reason I’m writing this by-now-rambling entry is to point you to an interesting call for submissions from the Defense Sciences Office. They’re looking for new drugs or technologies in their “Metabolic Dominance” program, the goal of which is thus:
The Defense Sciences Office is interested in proposals to develop innovative science and technology capable of affording superior physiological qualities to the warfighter. The vision for the Metabolic Dominance Program is to develop novel strategies that exploit and control the mechanisms of energy production, metabolism, and utilization during short periods of deployment requiring unprecedented levels of physical demand. The ultimate goal is to enable superior physical and physiological performance by controlling energy metabolism on demand. An example is continuous peak physical performance and cognitive function for 3 to 5 days, 24 hours per day, without the need for calories. Continuous exertion over numerous days is currently limited by: 1) the ability to transport and ingest adequate calories and/or effectively access stored calories (e.g., adipose, glycogen); 2) available training time; extended training periods are required to adapt muscle and mitochondria to meet intense physical loads; and 3) the ability of physiological systems to rapidly recover after extended, repeated bouts of physical exertion.
Squint a bit, and that almost reads like the text on the back of a workout pamphlet from the New York Sports Club.
Unless you’ve spent the last couple of years on the moon, you know that Google is now the world’s most important research tool. Students use it to research their papers, jilted lovers use it to stalk their exes — and journalists use it for just about everything.
That latter class may be a bit of problem, if you believe Lionel Beeher. He wrote a hilarious rant on the MediaBistro site pointing out that journalists have begun to cite Google results as evidence of a subject’s importance. The more hits something comes up with, the more culturally significant it must be, right? Beeher cites hilarious examples of this journalistic logic:
Take the February 2 issue of The New Yorker, for example, which features not just one but two examples of reportorial Googling to gauge a story subject’s popularity. First, TV critic Nancy Franklin cites Google in her article “L.A. Love” for, of all things, comparing the relative popularity of naked men and women. “A Google search for ‘naked men’,” she writes, “yields about six hundred thousand results; ‘naked women’ yields more than a million.” Ergo, the female body must be more desirous than the male’s. Case closed. Why? Well, because Google said so.
Franklin’s colleague Michael Specter couldn’t disagree. After all, he relies on a similar gambit in his story “Miracle in a Bottle” to gauge the popularity of the diet drug Zantrex. “If you type ‘Zantrex’ into Google,” he writes, “more than a hundred thousand citations will appear.” Though he preceded the sentence with evidence and statistics of the drug’s increased use, Specter seemed worried that in this dot-com age, Internet-savvy readers would be left unconvinced without hard search-engine evidence. Scientific studies as proof? Eh. Web searches? Now you’ve convinced me.

During the dot-com boom, software engineers became celebrities, fêted by the press. Back in 400 B.C., another class of technicians rose to rock-star prominence: Catapult engineers. Catapults were the WMDs of the preChristian era, revolutionizing war by allowing armies to destroy city walls — and lob the flu-infected severed heads of vanquished foes back into their loved one’s front yards. Nice.
Anyway, Serafina Cuomo, of the Imperial College London’s Center for the History of Science, recently wrote a paper for Science called “The Sinews of War: Ancient Catapults”, which be the coolest title of any academic paper ever. The official term for catapult science is “belopoietics” — with poietike meaning “making of”, and belos meaning “projectile or projectile-throwing device”. Apparently, the big scientific breakthrough was when early scientists realized that all parts of the catapult were proportional to the torsion springs. Once they figured that out, they had some pretty badass stuff on their hands — as an excellent story in National Geographic News reports:
The fearsome machines terrorized battlefields and sieges until the proliferation of gunpowder. Their power was impressive and terrifying. Roman catapults could hurl 60-pound (27-kilogram) boulders some 500 feet (150 meters). Archimedes’ machines were said to have been able to throw stones three times as heavy.
(Thanks to SciTech Daily for this one!)

We could have seen this one coming a mile away. The British company Link 77 has been having much success with Natachata, a chatbot it created that can talk dirty via SMS. People are, quite unsurprisingly, willing to pay per message for steamy chat while locked in boring day-long sales meetings.
Mark Ward of the BBC has a story about it today, with a funny example of a piece of chat:
barry says: “Hello how are you”
Julia says: “Hello, barry”
barry says: “Are you a virgin”
Julia says: “As far as you’re concerned, barry, I always will be”
What’s particularly interesting is that the inventors have grokked some of the Turing peculiarities of SMS — i.e. the stuff a ‘bot has to do to seem human in that medium. Like the popular Alice or Eliza ‘bots, Natachata pulls its responses from an enormous 100,000-strong library of contextualized responses, and can “remember” a few basic facts like the name of who it’s talking to. But the fun part is that once it generates an appropriate response, it “turns it into text slang” and “adds spelling mistakes” — crucial aspects of seeming “real” in SMS-speak. “It even adds a random delay to the return message because, if they were fired back too quickly, people would guess that they were computer-generated,” the BBC notes.
(Thanks to Techdirt Wireless News for this one!)

J.P. Brown is an archaeological conservator at the Field Museum in Chicago. But in his spare time, he builds some of the most dementedly advanced robots you’ve ever seen, using Lego Mindstorms. That robot above? It can solve a Rubik’s Cube puzzle. If you check out his site, you can see Brown’s complex descriptions of the engineering difficulties he faced — not the least of which was creating Lego robot grips strong enough to manipulate the cube. He’s also posted mindblowing videos of the robot in action.
Briefly, the software sends a message to the top RCX asking it to present one face of the cube to the video camera. The computer captures a frame from the video camera, and scans a 50x50 pixel area of each color patch to find the median red, green and blue (RGB) color values for each color patch on the face. The RGB values are converted to CIE X Y y coordinates, and then the CIE values are trigonometrically compared to the calibration values to find the closest match. The computer then asks the robot to show it the next face, and the process is repeated until all the faces have been scanned.
Consider the awesome circularity of this thing: A toy that can solve a toy. I’m in love.
This reminds me of why Lego may be the best toy ever to teach math, engineering, and logic. Any kid that plays with Lego has to confront the challenges of calculating how to add up multiple tiny shapes into a bigger one, usually with interesting questions of geometric symmetry thrown in, and the engineering demands of making a structure stable enough to be played with. And when you add in the Mindstorms programming language, you’ve basically got something that is essentially a complete curriculum in way-kewl geekitude.
Even before Mindstorms came along with an official coding language, Lego had many connections to the programming mentality. Brown himself has a superb nerd sense of humor, as I found when surfing his FAQ and discovered he’d written a description of his work like in NQC, one of the most popular Lego Mindstorms programming languages:
#define boredom_threshold 1
#define client_lag 35
#define work OUT_A
#define alive true
int meeting_lag;
task main()
{
while( alive ) {
crisis_level = Random( meeting_lag );
Wait( boredom_threshold + crisis_level );
On(work);
do {
Wait( Random( meeting_lag ) );
—crisis_level;
} while( crisis_level > 0 );
Off( work );
}
}

I was going over to Salon to read an article, and since I don’t have a subscription, I had to click on an ad and view it. What popped up was an extremely nifty Flash ad by General Electric: A string of water bubbles that you can “play” to produce notes on a violin. (There’s a screenshot of it above.) I messed around with it for a few minutes and soon was able to play quite complex melodies. And I thought, damn, now this is what more online ads ought to be doing — producing fun, engaging, quick-hit interactive experiences. It’s a superb little bit of work: Part ad, part game, part instrument.
Go try it out! Hint: To play individual notes, sweep up from below to touch the bubble you want. By the way, going to view the ad will also put money in Salon’s pockets, so you will be supporting independent journalism by playing music. How often do you get to do that?
Apparently there’s a new theory that says the universe will end with a totally outta-control explosion. Scientists are calling it “The Big Rip”, and it’s based on theories that the universe has “phantom energy” in it that helps explain why the universe is expanding.
There’s a great story on it in today’s New York Times, which explains our doom. Billions of years from now, apparently, phantom energy will be pushing the galaxies apart so quickly they’ll be near the speed of light — and the sky will go dark. The acceleration will demolish the galaxies:
About 900 million years later, about 60 million years before the end, our own Milky Way galaxy will be torn apart. Three months before the rip, the solar system will fly apart. The Earth will explode when there is half an hour left on the cosmic clock.
The last item on Dr. Caldwell’s doomsday agenda is the dissolution of atoms, 10-19, a tenth of a billionth of a billionth of a second before the Big Rip ends everything.
“After the rip is like before the Big Bang,” Dr. Caldwell said. “General relativity says: “The end. Time can’t evolve.”
The best part of the story is where the physicists basically admit that yeah, given how incredibly weird phantom energy is, it probably allows for things like antigravity and wormhole-based time machines. Antigravity and time machines, people. God DAMN do I love modern physics.
The Times’s web site gets bonus points for the driest copywriting on the planet: Attached to the news story is an “Interactive Graphic” illustrating “A New View of Doomday”.
By now, you’ve probably heard about the guy who put his mobile phone number — 867-5309 — up for sale on Ebay. Since that’s the number made famous by the Tommy Tutone hit song, it has been receiving massive bids: When I last checked in, it was going for $80,700. When I blogged about this a few days ago, I noted that customers do not actually own their phone numbers, and suspected that the phone company might step in and say, “hold it, we ought to get any cash for the sale here.”
Whaddya know. In an interview with Newsday, Verizon said such sales aren’t allowed:
But there’s a question of whether the number can even be transferred to the winner once the auction ends Feb. 22. Verizon says there’s no question: It can’t. Individuals do not have ownership of the numbers given to them, a Verizon spokesman said.
… and sure enough, if you check the item itself, it’s been taken down.
(Thanks to Boing Boing for this one!)

Some people like to buy knickknacks on Ebay. Some people like to buy a lot of knickknacks on Ebay. And some people function like the black holes of knickknackery, acquiring so many metric tons of ceramic gnomes and “glass art” that their homes develop their own fields of gravity and exert a small but measurable pull on the moon.
This guy’s mother falls into the third camp. So he went onto the Something Awful forums and posted a handful of pictures that function as a horrified tour of his mother’s house, complete with hilarious captions. The snapshot above is from his mother’s living room, where she keeps her paperweight collection. But my personal favorite is the murky picture of her bedroom, which is crammed full to the ceiling with Fedex boxes. The caption:
And here’s my mom’s bedroom. You were probably expecting a bed or something. It’s there, somewhere underneath all those boxes. My mom decided storing this stuff is more important that having a place to sleep. So where does my mom sleep? Remember that 2/3rds of a couch back in the living room? Yep, every night. No I don’t know what’s in any of these boxes either. Most of them are from eBay and have never been opened, just put straight on the pile.
(Thanks to Rob for this one!)

This is wonderfully demented: Steve, a programmer with Sim Slice, has released Slice City — a version of Sim City which is played inside The Sims. As Boing Boing notes, “that means that your simulated people can simulate being the mayor of a simulated city.”
Wired News wrote a piece about it:
Just like in The Sims, attention to detail breeds success and reward, while inattention breeds disaster.
“The Sims must routinely refurbish the buildings to keep the citizens happy, or just let them deteriorate and force the citizens to become unhappy and move away,” says Alvey. “Happy citizens go to work and pay taxes, which the Sims collect as revenue. The higher the profits, the more attractive the city becomes, so more citizens will move into it.”
Worlds within worlds within worlds. I love how Slice City riffs off the old science-fiction conceit, in which a scientist peers into a microscope and discovers a tiny civilization at atomic size. Then the camera zooms waaaaaay out and — whoa! — you see that the scientist is himself part of an atomic-scale civilization being peered at by another, huger scientist, who is himself being peered at in turn by another … and so on, and so on.
Recursion is one of the neatest and freakiest intellectual concepts there is.
(Thanks to Boing Boing for this one!)
Astronomers have just discovered that at the heart of the burned-out star “BPM 37093”, there is a diamond that weighs 10 billion trillion trillion carats. That’s one followed by 34 zeros. As the Sacramento Bee reports:
The heart of that burned-out star with the no-nonsense name is a sparkling diamond that weighs a staggering 10 billion trillion trillion carats. That’s one followed by 34 zeros.
The hunk of celestial bling is an estimated 2,500 miles across, said Travis Metcalfe, of the Harvard-Smithsonian Center for Astrophysics.
The “Dream Income” blog is devoted to archiving spam. Actually, the posts are nothing more than the header to the spam, then the message text — as if the spam itself were writing the blog.
It’s quite hilarious to look at, partly because it looks like a real blog, written by a real person. And that reminds us of the most salient fact about spam, which is that quite apart from it being a huge annoyance, it’s also the world’s largest and most successful Turing Test ever: A mass communication by robotized life forms desperately attempting to pose as human.
More significantly, the blog rocks because it is keeping an archive of spam. That’s actually a rather valuable service. Because who saves spam? Hell, I’m one of the few freaks that actually regularly reads his spam, just because I’m interested in it; but not even I save copies of them. The end result is that this no central “Library of Spam”; this enormous cultural explosion of hucksterism is not really being recorded anywhere, and in a purely academic sense, that’s sad. It’s the same way many pieces of pop culture were treated. Public libraries didn’t save copies of comic books, penny dreadfuls, or pop CDs either, and so much of that incredibly rich history is hard to find too.
(Thanks to Jonathan Korman for this one!)
As you may know, “number portability” has arrived for mobile phones — so that you can transfer a number from one phone to another. This has created an interesting side effect: People with particularly cool phone numbers are putting them up for sale to the highest bidder.
On Ebay today, someone is auctioning their mobile number “867-5309” — which was, of course, made hummably famous by the Tommy TuTone hit “Jenny (867-5309)”. It’s available in the 212 area code. When I last checked in, the bids had hit $56,000. Holy moses.
What’s particularly interesting is the attitude of the seller towards the number, as witnessed by the way she or he describes the “item”:
**I currently am the owner of 212-867-5309. I will transfer the number to the highest bidder.
**Number portability has allowed me to put this up for sale.
The thing is, nobody owns their phone number. It’s a piece of identifying data the phone carriers temporarily give to you, but they could revoke it at any point in time. Check your mobile-phone contract if you don’t believe me. (Actually, you’re carrying lots of things you don’t own. That bank card in your pocket? It’s the property of the bank, merely on loan to you while you have an account with them.)
But the point is, people believe that they own these things — so they treat them like property even if they aren’t. In the case of mobile numbers, this is likely to lead to some quite interesting culture clashes. What’s going to happen when mobile-number auctioning becomes a really big thing? Will Verizon and Cingular and Sprint and all the other carriers suddenly go, “whoa, hold a second, we should be getting the money for these sales”? Or will they consider it a sort of unavoidable usage culture that is basically free advertising for the coolness of mobile phones? It’s much like the fights that have cropped up in the world of online games like Ultima Online or Everquest, where the players began treating their virtual swords, castles and characters as a form of property, and selling them on Ebay — utterly without the consent of the companies.
** UPDATE: As I suspected, Verizon has yanked this auction — you can read my blog posting about it here.

Yikes. Over at Boing Boing, a guy sent in a picture of a handheld electronic game that a friend of his brought back from Taiwan about six months after 9/11. It’s called “Laden vs. USA,” and a closeup photo of it is here. No word on what the point of the game is, but a quick Google search indicates that this game has actually been manufactured several times — on this blog, there’s a photo of a slightly differently-shaped handheld unit that’s also called “Laden vs. USA”. (And another, clearer shot of the game pictured above is here.)
It’s a pretty bleak specimen, but in a strictly academic sense, this is an interesting example of the trend towards using games as a form of political commentary. In this case, however, I suspect the motivation is just good old-fashioned profiteering. It’s unlikely that the game has any political content specific to Al Qaeda or the USA. On the contrary, it’s probably just some entrepreneur who bought a few truckloads of a generic war-like “shoot the soldiers” game; there are hundreds of these things produced every year by electronics sweatshops in Asia. Then they printed some labels to “rebrand” the generic game with a purported bin Laden theme, slapped ‘em on the units, and sold them.
Not that this excuses the creepiness of the game, but it makes it rather unlikely that it has anything to do with actual terrorist networks.
A while ago I wrote about bluejacking, a fun way of using Bluetooth to zap a message onto the screen of any nearby Bluetooth-enabled mobile phone. But now there’s a new technique that’s much nastier: Bluesnarfing. Bluesnarfing is a technique for wirelessly reaching inside a Bluetooth phone and stealing any contact information stored in it.
It was discovered by a security officer in the UK who was testing the security of some Bluetooth handsets. As ZDnet reports:
Laurie said he discovered the problem when he was asked to test how safe Bluetooth devices actually were. “Before we deploy any new technology for clients or our own staff, one of my duties is to investigate that technology and ensure it is secure. Actually rolling your sleeves up and looking at it, not just taking the manufacturers’ claims at face value. When I did that, I found that it is not secure,” he said.
According to Laurie, he can initiate a bluesnarfing attack from his laptop after making a modification to its Bluetooth settings: “It is a standard Bluetooth-enabled laptop and the only special bit is the software I am using in the Bluetooth stack. I have a modified the Bluetooth stack and that enables me to perform this attack,” he said.
Bluesnarfing has huge potential for abuse because it leave no trace and victims will be unaware that their details have been stolen: “If your phone is in your pocket, you will be completely unaware,” he said.
This is an interesting gloss on the posting I wrote yesterday about cracking a system to try and examine its security, or lack thereof. In this case, a security official tried to invade a system — and in doing so, usefully exposed a problematic vulnerability.
I just noticed this now — over at Boing Boing, Cory Doctorow wrote an incredibly nice comment on my piece about virus writers! He goes on to offer a interesting critique of the piece based on a particular issue it raises: Whether computer code is protected as free speech. As Cory wrote:
Clive touches on, and dismisses the free-speech arguments for publishing malware code (interestingly, he does so without any quotes from legal scholars and impact litigators who work on First Amendment issues, and so ends up eliding the nuance in the argument and presenting a somewhat blunted picture of the issue) and only lightly touches on the far more important notion of legitimate security research.
If, as Schneier says, “Any person can create a security system so clever s/he can’t think of a way to defeat it,” then the only experimental methodology for evaluating the relative security of a system is publishing its details and inviting proof of its flaws — proof readily embodied in malware.
Codebreakers and worm-writers are the only mechanism we know about for reliably strengthening systems, and the idea that they should refrain from publishing their research in order to keep us safe is fundamentally flawed, since it depends on the idea that malicious people will never be clever enough to independently reproduce their techniques, and that the public is better served by remaining ignorant of the potential risks in the systems they’ve bought than by being exposed to the evidence of the rampant flaws in those systems.
This notion falls flat when considered in light of the real world. If a developer was building condos whose doors could all be unlocked with an unbent paper-clip, this line of reasoning demands that the person(s) who discover this should keep mum about it, in the hopes that no bad guy ever catches on. In the real world, the best answer is usually to scream about this to high heaven, so that the bad developer can’t silence you and cover his ass, and so that his customers can get their locks fixed.
This is an excellent debate. But I don’t think my article dismisses the free-speech argument. Indeed, quite the opposite — it explicitly states that code is a form of speech. As I wrote …
… in most countries, writing viruses is not illegal. Indeed, in the United States some legal scholars argue that it is protected as free speech. Software is a type of language, and writing a program is akin to writing a recipe for beef stew. It is merely a bunch of instructions for the computer to follow, in the same way that a recipe is a set of instructions for a cook to follow.
Cory’s quite right that I didn’t actually quote any legal scholars or free-speech experts in the piece, though I certainly have interviewed plenty of them on this issue (including, back when I was writing about the DeCSS trial, the insanely brilliant Dave Touretzky).
I think Cory may be confusing my discussion of the ethics of virus writing with the right to compose malware. My article points out that the ethics of virus-writing are considered, by many, to be somewhat suspect. That doesn’t dismiss the point about the free-speech argument for writing computer code. Quite clearly, code is a form of speech — and for the record I would be very, very glad to see it thusly protected! (Not the least because, while being myself only a very crappy and very occasional programmer of the lamest computer languages in existence, I find programming a superbly intellectual endeavour.)
But just because one has a right to do something does not mean it’s ethical to do it. (And vice versa — there are, sadly, plenty of people in jail for things that were against the law but were not even vaguely unethical, including much civil disobedience.) Rights and ethics are very different things. What my article was in part trying to explore were the complex ethics of virus writing.
As Cory pointed out, one can also make a good ethical case in favor of virus writing. I, too, pointed out the argument:
Indeed, a number of them say they are making the world a better place, because they openly expose the weaknesses of computer systems. When Philet0ast3r or Mario or Mathieson finishes a new virus, they say, they will immediately e-mail a copy of it to antivirus companies. That way, they explained, the companies can program their software to recognize and delete the virus should some script kiddie ever release it into the wild. This is further proof that they mean no harm with their hobby, as Mathieson pointed out. On the contrary, he said, their virus-writing strengthens the ”immune system” of the Internet.
Having said that, it is true that I presented the devil’s-advocate side: That widely publishing your virus code can fall into an ethical grey area. That’s because viruses behave in ways rather different from other types of code. Cory quotes Schneider to point out a well-known security fact: That one good way to improve the security of a computer system is for smart outsiders to examine it carefully and discover its weaknesses. That’s why open-source code like Linux is so stable; tens of thousands of smart geeks have looked at the code and immediately publicized any weaknesses they find. That’s also why smart goverment agencies and companies hire tiger teams to try and break into their own systems. It’s a great way to probe your own vulnerabilities.
Viruses and worms are a bit different, though, I think. Attempting a series of hack-attacks on a particular system to try and uncover its weaknesses is a stable, controlled experiment. You can run the experiment in such a way that you don’t actually hurt anyone. But when viruses and worms are released, they’re inherently uncontrolled. They interact with thousands of unknown computer systems with unknown configurations; there’s simply no way to fully predict what’s going to happen. They might be harmless. Or they might screw up the 911 system in a city, as Slammer did. There are plenty of ways to test a system with a single hack attack. You can prove that backdoor exists by invading it on a single machine; no harm done. But there is no way to definitively prove a virus would spread the way you think it would without releasing it — and that’s an inherently chaotic endeavor.
Yet I still don’t think one should be prohibited from writing worm and virus code — because as Cory says, the code can be a good way to show, on paper, that a vulnerability exists that ought to be patched. The grey area is: How to publish the findings? If you put the full code to your worm up online, you can be pretty certain someone will release it. And though publishing may indeed be your legal right, in this context, it’s also an ethical decision. Are there other ways to inform the world about a worm-related vulnerability you’ve discovered? Publish only the most relevant parts of the code? That might not be a bad idea, since script kiddies won’t be able to write the rest of the code necessary to get the worm up and running; a smart security official, however, could look at those few lines of worm code and immediately grok the vulnerability they need to patch.
The counterargument would be that “software companies drag their heels — nobody would ever really fix a vulnerability until they’ve had it literally slammed in their faces. You have show the full worm code — hell, it probably has to be released in the wild — before they’ll really take it seriously.” Fair enough. The vulnerability that the Slammer worm exploited had been known for months; people only got serious about patching it once they’d seen how much damage a worm could do. And, once again, one ought indeed to have the free-speech right to publish a worm. But I don’t think exculpates you from the ethical aspects of the debate. Rights are clean and simple; ethics are super-messy.
Since Cory opened his posting about my article with an incredibly nice compliment about my writing, I’m going to close with one about his: Readers! If you are still with me here, DO NOT WALK but RUN to the nearest bookstore and get a copy of Cory’s latest novel, Eastern Standard Tribe. He is easily one of the most talented science fiction writers I’ve ever encountered, and my shelves are groaning with the stuff. (His last novel Down and Out in the Magic Kingdom fried my noodle and inspired a zillion interesting conversations about the future of the reputation economy.) Go. Now!
Hmmm. Movable Type is acting up and not letting me rebuild my site. I’m not sure why, so I’m testing with a test posting here!

I bet you did not know that Feb. 5 was the first-ever “International Robot’s Day”.
Actually, neither did I. In fact, probably the only people who knew about it were the Euroweenie artists who stitched together a bunch of global events into this cyborgian celebration. But, since I like robots and have a couple of them myself — in fact, my Roomba is currently slaving away at cleaning the living room as I type — I heartily approve.

Brendan Dawes, an insanely brilliant programmer, has created Cinema Redux — an application that produces a massive poster composed of tiny snapshots of each scene in a film. In essence, he produces a huge image that lets you “see” the entire film in one eyeful. He wrote a really nice description of the aesthetic purpose of his project, so here it is in his own words:
The end result is a kind of unique fingerprint for that film. A sort of movie DNA showing the colour hues as well as the rhythm of the editing process. Compare Serpico to The Conversation. You can see there’s far more edits in Lumet’s classic compared to the more gentle slower pace of Coppola’s Conversation. This is also down to the editing style of Walter Murch who prefers to only make cuts when absolutely necessary.
That picture above is a small chunk of the poster of Alfred Hithcock’s Vertigo. You can see more examples of the images here, and even buy a poster of one of them.
(Thanks to the J-Walk blog for finding this one!)
Check out the Acme Labelmaker, which lets you create your own sticky-tape-style labels to slap all over your web site.
(Thanks to the J-Walk blog for this one!)
As I’ve written before, we now live in the Turing age. Every time we open our email boxes, we’re forced to conduct dozens of Turing tests, trying to quickly figure out which of the pieces of email are from real humans, and which were sent by spambots.
This battle has now claimed its first linguistic casualty. It occurred to me yesterday that you can no longer send an email to anyone with the sole word “hello” in the message header.
Why? Because the email recipient is almost certain to throw out your email before reading it. And why would they do that? Because the MyDoom virus has been flooding our inboxes with endless copies of itself, half of which say merely “hi” or “hello” in the message field. I personally have been getting between 20 and 60 copies of MyDoom every day for the last two weeks. So as I go through my email every day, numbly disposing of the 70 to 80 per cent of which is spam (and I get about 300 messages a day), I’m almost certain to throw out anything with “hi” or “hello”.
The other day, I got an email from a friend saying, hey, did you get the email I sent you last week? And I hadn’t. I didn’t remember reading anything from him. He insisted he’d sent me an email, so I asked him, hey, just out of interest, what did you put in the message line? Oh, I said “hello,” he replied.
Heh. That’s the problem. These days, saying “hello” and “hi” instantly and definitively marks you as a spambot. I, and most other people on the Net, will immediately delete your mail and won’t even waste the microsecond necessary to glance over to see which email address the email has come from.
So here’s a tip for anyone who’s trying to email me. If you want to appear human-like, put a human-like message header on your email. And that means you can’t say just “hello” or “hi,” because that no longer qualifies as a human-like message.
I blogged a few days ago about Georgia outlawing the use of the world “evolution” in their high-school biology classes. Georgia officials rather shamefacedly backtracked a couple of days later and reinstated the word, which is cool. But over at Culture Raven, my friend Erik points out an interesting nuance that’s often ignored in the polarized evolution/creationism debate: That even amongst the ranks of scientists, there’s still substantial debate about evolution. Steve Fuller argues this in his book Kuhn vs. Popper: The Struggle for the Soul of Science, which Erik parses thusly:
Physicians, entomologists, zoologists, and biologists seem predisposed to rejecting Darwinism. They work with these complicated, juicy, goofy, living entities whose personality, animation and complexity just don’t seem reducible to stochastic processes like mutation and natural selection …
Lots of real smart-type folks have shied away from full-on Darwinism and have tried to prove that complex “organic forms,” be they societies or species, establish their own “pattern of development against external environmental pressures.”

For years, scientists have pondered the mystery of how carrier pigeons navigate back home. Do they have special inner-ear navigational systems? Do they sense the magnetic fields of the earth? Do they perform some complex on-the-fly calculus using the position of sun?
Nope. Turns out they just follow the roads, like everyone else. A bunch of scientists at Oxford university in London attached teensy GPS trackers to pigeons and found the birds flew quite precisely along the lines of major highways. As professor Tim Guildford told the Telegraph:
“In short, it looks like it is mentally easier for a bird to fly down a road and then turn right. They are just making their journey as simple as possible”.
His team carried out dozens of tests with pigeons in Oxfordshire, releasing them between 10 and 20 miles from their lofts, each with a tiny GPS tracking device attached to their backs. Matching their routes, they found most flew straight down the A34 Oxford bypass.
“It was almost comical watching one group of birds that we released near a major A road. They followed the road to the first junction where they all turned right, and a couple of junctions on, they all turned left”.
This Sunday, the New York Times Magazine ran a feature I wrote on the world of virus-writers. The story is on their site but you have to pay to see it, so I’ve put the entire text below for free archiving:
The Virus Underground
Philet0ast3r, Second Part to Hell, Vorgon and guys like them around the world spend their Saturday nights writing fiendishly contagious computer viruses and worms. Are they artists, pranksters or techo-saboteurs?By Clive Thompson
This is how easy it has become.
Mario stubs out his cigarette and sits down at the desk in his bedroom. He pops into his laptop the CD of Iron Maiden’s ”Number of the Beast,” his latest favorite album. ”I really like it,” he says. ”My girlfriend bought it for me.” He gestures to the 15-year-old girl with straight dark hair lounging on his neatly made bed, and she throws back a shy smile. Mario, 16, is a secondary-school student in a small town in the foothills of southern Austria. (He didn’t want me to use his last name.) His shiny shoulder-length hair covers half his face and his sleepy green eyes, making him look like a very young, languid Mick Jagger. On his wall he has an enormous poster of Anna Kournikova — which, he admits sheepishly, his girlfriend is not thrilled about. Downstairs, his mother is cleaning up after dinner. She isn’t thrilled these days, either. But what bothers her isn’t Mario’s poster. It’s his hobby.
When Mario is bored — and out here in the countryside, surrounded by soaring snowcapped mountains and little else, he’s bored a lot — he likes to sit at his laptop and create computer viruses and worms. Online, he goes by the name Second Part to Hell, and he has written more than 150 examples of what computer experts call ”malware”: tiny programs that exist solely to self-replicate, infecting computers hooked up to the Internet. Sometimes these programs cause damage, and sometimes they don’t. Mario says he prefers to create viruses that don’t intentionally wreck data, because simple destruction is too easy. ”Anyone can rewrite a hard drive with one or two lines of code,” he says. ”It makes no sense. It’s really lame.” Besides which, it’s mean, he says, and he likes to be friendly.

I have always liked Ikea. I own several of their low-end bookshelves — those incredibly crappy ones that look as if the wood were composed of popsicles that had been ground up and injection-moulded into boards. They’re so lightweight they’ll tip over if you just stare at them hard enough. But what the hell: They’re cheap, and I bought them while a broke college student.
But apparently the men of America loathe Ikea. Their girlfriends keep dragging them out to buy potpourri bowls or faux-Chinese curtains or whatever, and the guys are starting to freak out. So as a public service, Matthew Baldwin at The Morning News recently wrote a survival guide for Ikea — in the style of a video-game walkthrough:
==========================
IKEA WALKTHROUGH v2.3.1
==========================IKEA is a fully immersive, 3D environmental adventure that allows you to role-play the character of someone who gives a shit about home furnishings. In traversing IKEA, you will experience a meticulously detailed alternate reality filled with garish colors, clear-lacquered birch veneer, and a host of NON-PLAYER CHARACTERS (NPCs) with the glazed looks of the recently anesthetized.
==========================
OBJECTIVE
==========================Your goal is to successfully traverse the five awesome worlds of IKEA before your patience runs out. On your first few tries this may seem like an impossible task, but with practice (and this IKEA Walkthrough!) you will soon be able to muster the sense of numb resignation necessary for victory.
In New York, many people were shocked by the recent accidental shooting of Timothy Stansbury Jr., a 19-year-old Brooklyn teenager, by a police officer. There are plenty of theories as to why the accident happened, but over at this week’s Village Voice, Erik Baard finds a possible explanation in an intriguing area: Neuroscience.
Baard discovers that there’s an emerging group of scientists who are studying the ways in which human neurological wiring can lead to fatal accidents with guns. Take the Stansbury case. The teenager was heading up a stairway onto the roof of a Brooklyn tenement, and about to open the door. The police officer, Richard S. Neri Jr., was on the rooftop and by sheer coincidence was on the other side of the door, about to open it himself. No one yet knows who precisely opened the door first, but if it was Neri, that might have set off a physiological chain reaction that led him to — quite unintentionally — fire his gun. Baard cites some recent research by Roger M. Enoka, chair of the department of integrative physiology at the University of Colorado:
[In} a recent paper for Law Enforcement Executive Forum, Enoka raises [an] intriguing idea. Our brain has a near compulsion for symmetry. When a signal is sent to one limb, a doppelgänger signal spills over to the other. This phenomenon is so powerful that Shi Zhou, a physiologist at Southern Cross University in Australia, reported to Exercise and Sports Sciences Reviews that limbs opposite to those being exercised also gained substantial strength.
It’s not clear who opened the rooftop door, but if Neri did, that could help explain what went wrong. “The action of opening a door with one hand can be sufficient to evoke a sympathetic contraction that is strong enough to cause the fingers in the other hand to squeeze the trigger and discharge a gun,” Enoka said.
This is damn interesting stuff, because it suggests two things. One is that some police who have discharged their weapons might well have never intended to do so. The second is that it “such shootings may be almost impossible to eliminate,” as Baard worries. He notes that police experts have suggested several ways of removing the element of surprise from policing — such as giving cops thermal scanners, so they can see how many bodies are behind a door. The less surprise they face, the more control their have over their hardwiring neurological responses.
None of this is to exculpate genuinely sloppy policing, of course. But I’ve interviewed officers in the past who’ve talked about the weird tricks your body plays on you when you’re in a dangerous situation, real or perceived. One police-studies academic told me he became worried when officers on his force were first issued guns with 14-shot clips, instead of six-shot pistols. The problem? When you’re terrified that your life is in danger and you fire your gun, there’s a natural impulse to simply squeeze the trigger again and again until all the bullets are gone. In that situation, a 14-bullet gun has a far greater likelihood of killing someone, where a six-shot pistol might only wound them. Of course, the whole point of police training is to prevent police from spastically emptying their entire gun — but in practice, it isn’t that easy to do.
Now that video games are becoming part of mainstream culture, you frequently see TV shows and movies where the characters are playing games and talking. It’s a brilliant device, because so many dramatically complex things going on: The characters are interacting with the game, interacting with each other, and interacting with each other about the game. (When my friend Greg and I play Smuggler’s Run, we’ll frequently scream at each other stuff like “Hey! Those are my drugs! GIVE ME BACK MY DRUGS.”) It’s no wonder Hollywood has discovered this lovely new staging ground for human emotion.
But there’s one problem: The buttons.
If you look closely at how the characters are manipulating the joysticks, it makes no sense at all. They’re usually twitching and spasming away, randomly twiddling the joysticks in a manner that less resembles actual game playing than a crystal-meth trip gone horribly, horribly awry. Over at Game Girl Advance, Kyle Herbert became so incensed at this trend that he wrote a hilarious attack on the surrealism of Hollywood gaming:
Even shows starring actors young enough to play video games on a regular basis fail miserably at depicting game playing correctly. Nearly once an episode on Fox’s The OCtwo of the main characters, Seth and Ryan (played by Adam Brody, 23, and Benjamin McKenzie, 25, respectively) can be seen playing what appears to be a PS2. These two actors undoubtedly grew up gaming, and have been playing games long enough to know the proper way of maneuvering a character in a game environment. Even from these two though we see the same tragic button mashing that would only result in a quick loss of lives and continues.
In gamer circles, “button mashing” is actually a cultural term: It stands for the sort of random hammering of the joystick that you see when a newbie picks up a game for the first time and doesn’t know what he or she is doing. But there is, of course, a good reason why Hollywood mashes so heavily. TV always draws life in broad strokes, amplifying activities to make them seem more exciting. Remember all those 50s shows where someone’s driving a car purportedly down a straight highway, while nonetheless psychotically swerving the wheel back and forth?
A couple of web guys are doing a version of the Bible as IRC-style chat. This, for example, is the end of Genesis; God has just arrived after Adam and Eve eat the apple:
* Jehova has joined #Eden
‹Jehova› what have you done?
‹Eve› it was the serpent!
‹Jehova› Serpent, schmerpent!
‹Adam› really!
* Jehova sets mode: -v Serpent
‹Jehova› fs
* Jehova sets mode: +b Adam!*adam@host1.10.1.genesis.com
* Jehova sets mode: +b Eve!*eve@host1.10.2.genesis.com
* Adam was kicked by Jehova (Get out!)
* Eve was kicked by Jehova (Get out!)
* Jehova changes topic to “and stay out!”
* Flamingsword has joined #Eden
* Jehova has left IRC (signed off)
Here endeth the lesson.
All joking aside, the Bible actually ports astonishingly well to the language of the Internet, partly because the central metaphors and conceits of each are oddly similar: Rooms opening and closing, access to elite areas granted or denied, obsessions with naming and true names, and everywhere the presence of language as an affective force. Computer code fits perfectly into the psychic headspace of Christianity, since it is a form of language that does things — like the word of the almighty, it’s both a metaphor and metonym. Northrop Frye called the Bible “the great code”, and only now am I realizing what a massively geeky in-joke that actually is.
(Thanks to El Rey for this one!)

Privacy freaks have always worried about Tivo, because the company’s technology allows it to closely monitor the viewing patterns of users. But here’s one interesting offshot of the snooping: Tivo executives discovered that the now-infamous Janet Jackson flashing incident was the most-viewed part of the entire Super Bowl — with Tivo users obsessively rewinding and reviewing that moment. It was so popular that it far, far outstripped any moment of actual football. Indeed, it’s the most-replayed moment Tivo has ever measured. As a Tivo press release notes:
The Jackson-Timberlake moment drew the biggest spike in audience reaction TiVo has ever measured. TiVo said viewership spiked up to 180 percent as hundreds of thousands of households used TiVo’s unique capabilities to pause and replay live television to view the incident again and again.
What’s more:
Commercials once again drew a bigger reaction from viewers than any of the action on the field … The ‘wardrobe incident’ during half time was the scene stealer of the Super Bowl,” said Marty Yudkovitz, President of TiVo. “In fact, the half time show during the Super Bowl is now running a close second to the commercials as the most compelling content for viewers. The actual contest on the field continues to be the secondary event during the Super Bowl.”
Of course, we hardly needed more evidence that the Super Bowl is less a game than a pure shot of American consumerism boiled down to a quintessence and freebased directly into the public’s motor cortex. But if we, uh, actually did need more evidence, there it is.

Heh. Genius web designer Matt Round has created a web page that presents you with various head shots of alternately scruffy and clean-shaven dudes. Then it challenges you to pick which ones are computer scientists who invented a programming language — and which ones are serial killers.
Normally, I’d pinheadedly object to the “bathing libel” — i.e. the familiar cultural assumption that programmers are unkempt freaks. But in this case, the quiz is so funny and entertaining that I’ll shut up.
(Thanks to Tribblescape for this one!)
There’s a superb piece in the New York Times today about lip-synching, and how most of today’s pop performers no longer sing live. There were a few particularly gorgeous moments:
One former record executive, who insisted that he not be named, recalled being in the front row for a Janet Jackson performance and seeing her count dance steps with her lips while her singing voice played over the public address system. (Her label, Virgin Records, did not respond to interview requests.)
On television today, some effort is still made to have performances seem live, but it’s often not very convincing. When Casey Spooner of Fischerspooner appeared on the British show “Top of the Pops” with Kylie Minogue, for example, he said he was asked to wear a bogus headset microphone. “There is no microphone,” he said. “She’s wearing, like, a coat hanger with a piece of electrical tape on it.”
If singers are not longer singing, this is because of a point so obvious the story almost neglects to mention it: That the central qualification for succeeding as a major pop performer these days is your ability to dance. When MTV first launched back in the 80s, performers used to bemoan the fact that “only attractive people would be able to make albums”. Ah, what a quaint concern. These days, being drop-dead gorgeous/handsome is a given; but even with that in hand, you’ll never crack pop’s top 40 without being able to gyrate like a Dallas Cowboy Cheerleader.
I remember the first time I saw Britney Spears, back in the late 90s when we was first, uh, busting out. She was on Saturday Night Live, and she performed a complex routine with four or five backup dancers. And I remember thinking, man, she looks really nervous — her eyes were glazed over like she couldn’t focus on anything. Then it occurred to me that, of course, she wasn’t nervous about singing badly: She was nervous about dancing badly. A lousy musical performance would be problematic; but a botched dance move would be complete and total career suicide, as the expression of wall-eyed panic on her face clearly illustrated. It kinda makes you think it would be a lot easier on everyone if she and her fans would mutually agree that nobody particularly cares whether or not she can sing live, and just have her smile and wave as she prances around, like one of the Rockettes, or Oxana Baiul.

A computer engineer in Holland, Michigan, has named his newborn son after himself — but rather than the suffix “Jr.”, he’s calling it “2.0”. As CNN reports:
Jon Blake Cusack talked his wife, Jamie, into naming their son Jon Blake Cusack 2.0.
Version 2.0 was born Tuesday at Holland Community Hospital, and the proud parents took him home Friday.
“I wanted to find something different to name him besides Jon Blake,” Cusack, who is self-employed with Westshore Design and Cusack Music, told The Holland Sentinel.
I, too, have an alphanumeric name: Officially, I’m “Thomas Clive Thompson III”. However, since it looks poncy beyond description to use the digits, I tend to leave ‘em out. I suppose if I ever have a son I could name him Thomas Clive Thompson v. 4.0, but that strikes me as really ill-advised: It’s almost always in the later versions that the code becomes complex and bloated, the bugs creep in, and everything crashes.
(Thanks to Boing Boing for this one!)
I'm Clive Thompson, the author of Smarter Than You Think: How Technology is Changing Our Minds for the Better (Penguin Press). You can order the book now at Amazon, Barnes and Noble, Powells, Indiebound, or through your local bookstore! I'm also a contributing writer for the New York Times Magazine and a columnist for Wired magazine. Email is here or ping me via the antiquated form of AOL IM (pomeranian99).
ECHO
Erik Weissengruber
Vespaboy
Terri Senft
Tom Igoe
El Rey Del Art
Morgan Noel
Maura Johnston
Cori Eckert
Heather Gold
Andrew Hearst
Chris Allbritton
Bret Dawson
Michele Tepper
Sharyn November
Gail Jaitin
Barnaby Marshall
Frankly, I'd Rather Not
The Shifted Librarian
Ryan Bigge
Nick Denton
Howard Sherman's Nuggets
Serial Deviant
Ellen McDermott
Jeff Liu
Marc Kelsey
Chris Shieh
Iron Monkey
Diversions
Rob Toole
Donut Rock City
Ross Judson
Idle Words
J-Walk Blog
The Antic Muse
Tribblescape
Little Things
Jeff Heer
Abstract Dynamics
Snark Market
Plastic Bag
Sensory Impact
Incoming Signals
MemeFirst
MemoryCard
Majikthise
Ludonauts
Boing Boing
Slashdot
Atrios
Smart Mobs
Plastic
Ludology.org
The Feature
Gizmodo
game girl
Mindjack
Techdirt Wireless News
Corante Gaming blog
Corante Social Software blog
ECHO
SciTech Daily
Arts and Letters Daily
Textually.org
BlogPulse
Robots.net
Alan Reiter's Wireless Data Weblog
Brad DeLong
Viral Marketing Blog
Gameblogs
Slashdot Games